Web ve mobil uygulamalar her geçen gün artarken, iletişim ve servis hizmeti olarak çok farklı işletim sistemlerinde ve farklı platformlarda hizmet vermektedir. Hizmet gizliliği, veri bütünlüğü ve servis sürekliliği kapsamında güvenlik önlemleri tasarımdan işletime kadar her noktada düşünülmektedir. Web ve mobil uygulamaların vermiş olduğu servisler, birçok farklı ortamlarda hizmet verdiklerinden çok fazla siber atak vektörlerine sahiptir.

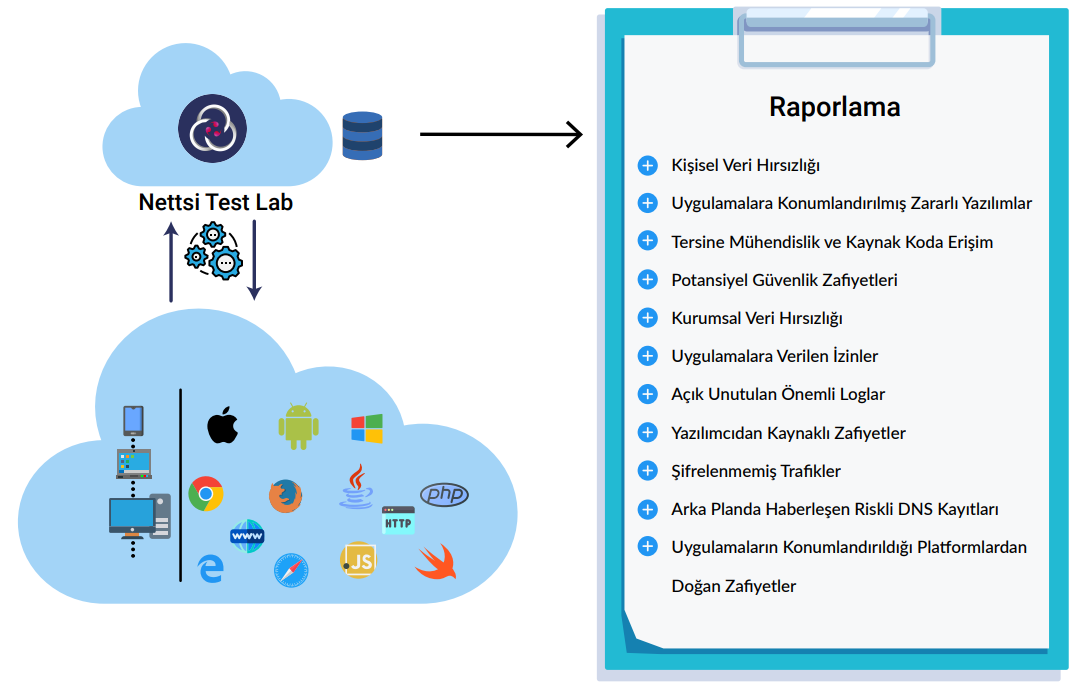
Kişisel ve kurumsal verilerin korunması kapsamında uygulamaların ataklara karşın güvenilirliği yanında uygulamaların kendisinin de güvenilir olması önemli olduğundan Web ve mobil uygulamaların zengin test laboratuvarlarında yetkin kadro ile analizlerinin gerçekleştirilerek bulguların raporlanması, uygulamaların güvenilirliği hususunda önem arz etmektedir.
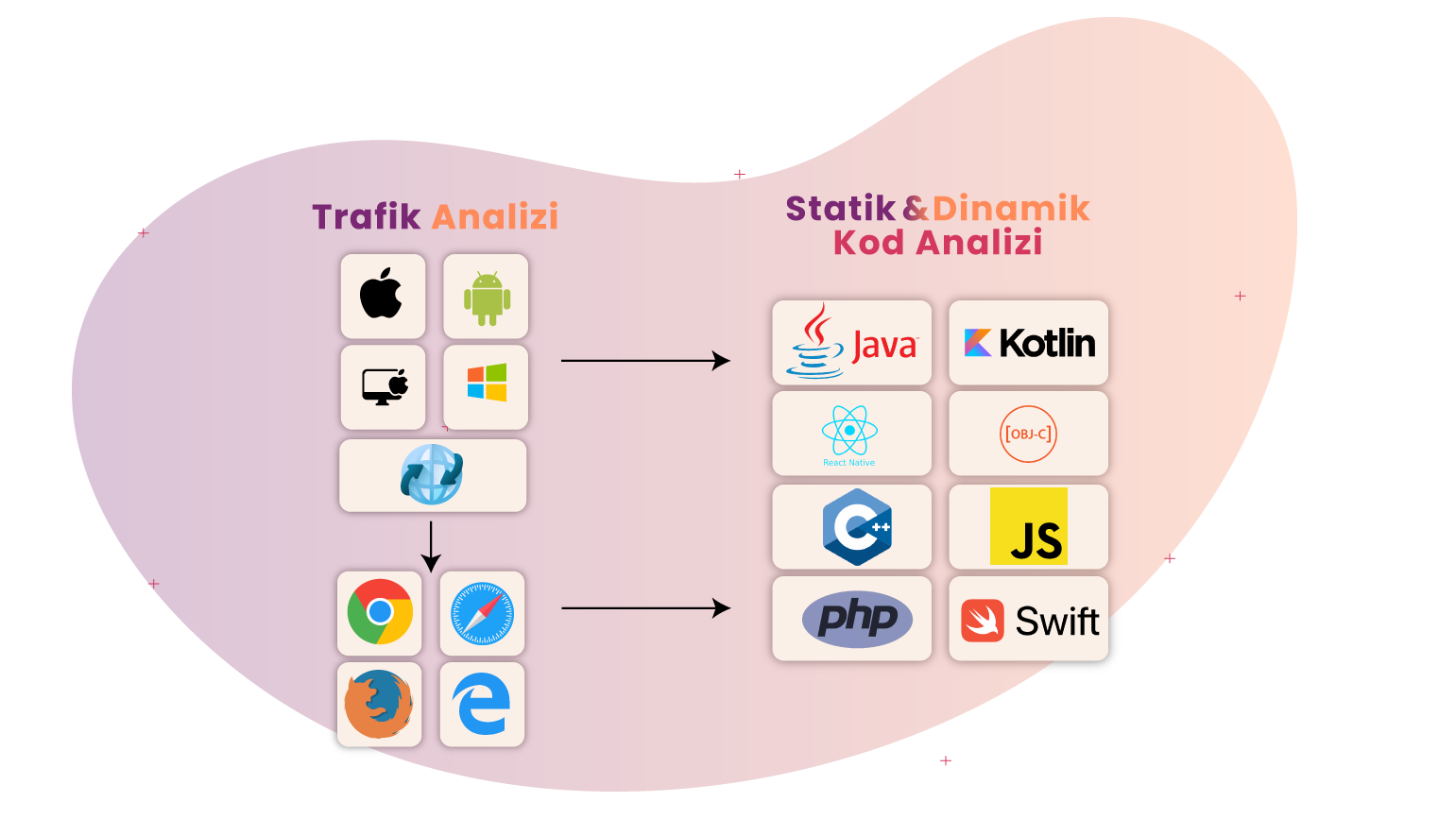
Web ve mobil uygulamalarda test ve veri güvenliği analizi; farklı platformlarda olası tüm senaryoların koşulup analiz edilerek çıktıların değerlendirilmesi ile yapılmaktadır. Kişisel ve kurumsal verilerin korunması kapsamında Web ve mobil uygulamalarda karşılaşılan zafiyetler ve uygulamaların veri hırsızlığı ele alınması gereken temel noktalardandır. Trafik analizi, statik ve dinamik kod analiziyle birtakım riskler açığa çıkmaktadır.
- DNS Kayıtlarında Anomali Tespiti
- Şifrelenmemiş Trafik Tespiti
- Hash Analizi
- Platformdan Kaynaklanan Zafiyetlerin Tespiti
- Zararlı Yazılım Trafik Tespiti
- Protokol Tespiti
- Uygulamalara Verilerin İzinlerin Analizi
- Yazılımcıdan Kaynaklı Zafiyetlerin Tespiti
- Veri Hırsızlığı Tespiti
- Uygulamanın Çalışması Esnasında Tetiklenen Kod Bloklarının Tespiti
- İkili (Binary) Enstrümantasyonu
- Logların Görselleştirilmesi